Securely Connect Remote IoT & Raspberry Pi With RemoteIoT VPC!
In an age defined by interconnected devices and data streams, how can we ensure the safety and integrity of our Internet of Things (IoT) ecosystem? Securing your remote IoT devices is not just a best practice; it's a fundamental necessity in today's digital landscape.
The pervasive nature of IoT, from smart home appliances to industrial sensors, has revolutionized how we interact with technology. However, this evolution has also created new vulnerabilities. Ensuring that your IoT devices, often deployed in remote locations, are protected from unauthorized access and data breaches is paramount. This article delves into the practical aspects of securely connecting remote IoT devices, providing a comprehensive guide to understanding the tools, strategies, and best practices needed to fortify your digital fortress.
Before diving into the specifics, it is vital to recognize the foundational role of security in the IoT landscape. In today's interconnected world, where data breaches and cyber threats are constantly evolving, a proactive approach to security is non-negotiable. Neglecting the security of your IoT devices can have severe consequences, ranging from data loss and privacy violations to disruptions in critical operations and financial setbacks.
- Telugu Movies Movierulz Updates Latest News Streaming Info
- Latest Updates Movierulz Movie News Reviews
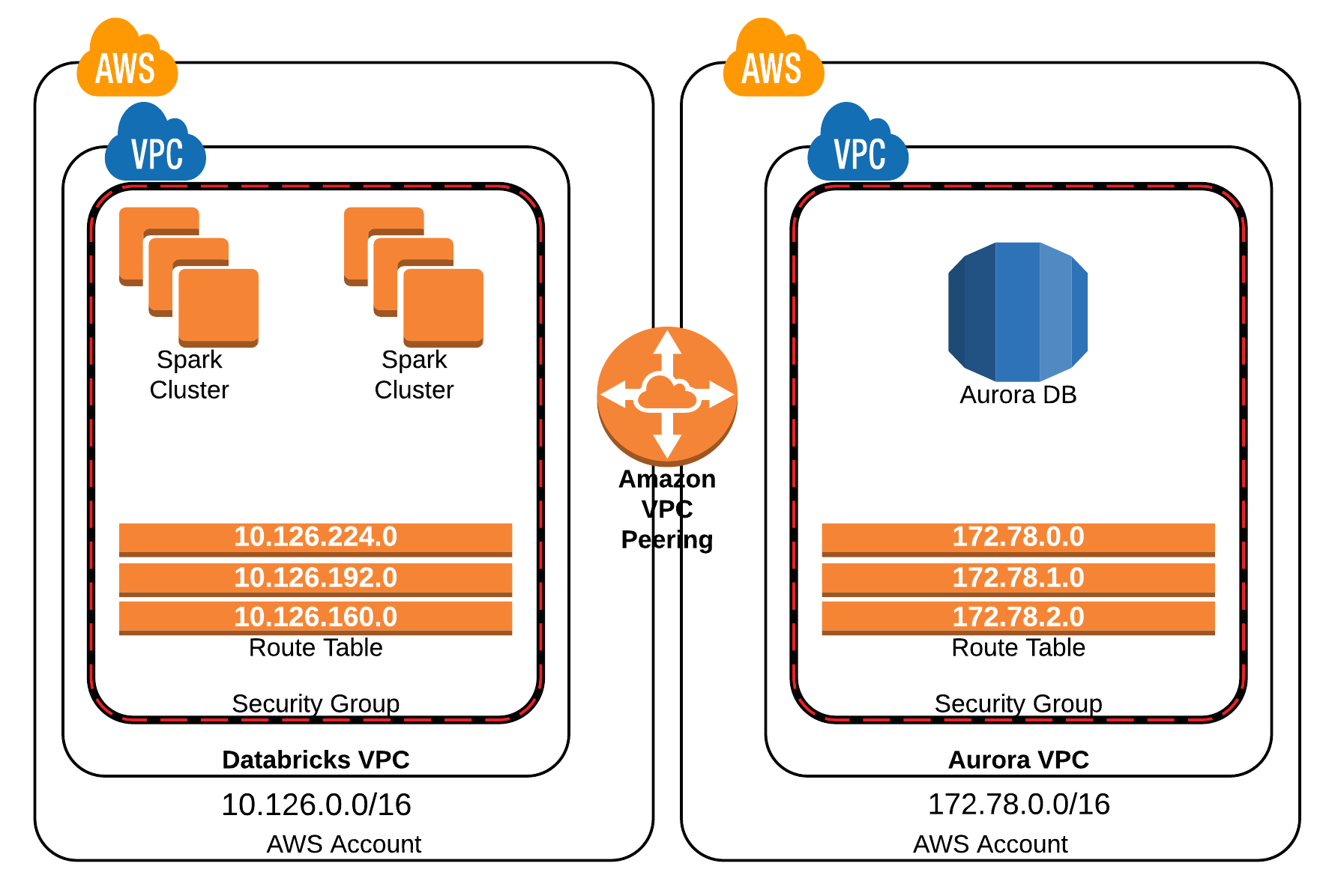
This is where the concept of a Virtual Private Cloud (VPC) comes into play. A VPC acts as a private network within a public cloud, providing a secure and isolated environment for your resources. When applied to IoT, a VPC enables you to establish a secure connection between your devices and the cloud, safeguarding data transmission and access control. Through the use of technologies like a Raspberry Pi, which serves as a gateway, and the tools and configurations of RemoteIoT, this is achievable.
Imagine that, with RemoteIoT, you can securely and directly connect your Raspberry Pi and IoT devices from any location, operating as if they were within a local private network. This eliminates the need for costly subscriptions and additional hardware, offering a cost-effective and efficient solution. The RemoteIoT Peer-to-Peer (P2P) VPC network, in particular, facilitates direct connections, optimizing data communication speed, reducing latency, and maximizing bandwidth for data transmission between your IoT devices. The orchestration of devices to the RemoteIoT VPC is a crucial step, ensuring that all data transmitted is encrypted and protected.
Here's a breakdown of the key concepts:
- Where To Watch Stream Movies Your Ultimate Guide 2024
- Movierulz 2025 Latest South Indian Movies News Must Know
- RemoteIoT VPC: The primary focus of this article is the RemoteIoT Virtual Private Cloud. It provides a secure, isolated network for your IoT devices, ensuring protected data communication and access control.
- Raspberry Pi: Acting as a gateway, the Raspberry Pi is the backbone to securely connect your remote IoT devices to the cloud.
- Secure Connections: This guarantees encrypted and secure data transmission, preventing unauthorized access and data breaches.
Now, let's dive deeper into the application of RemoteIoT and its importance, especially when combined with AWS services. For modern businesses, connecting remote IoT devices to the AWS VPC securely is a critical task, especially when leveraging cloud infrastructure. This is particularly important for ensuring robust data protection and system integrity. Understanding how to set up a secure connection is more crucial than ever for protecting sensitive data and maintaining system integrity. The information within this article will provide a valuable understanding of the best practices, tools, and strategies to ensure a secure connection to your RemoteIoT VPC while maintaining high performance and reliability.
Here's a look at the potential challenges you may face:
- Connectivity Issues: Encountering problems such as "Securely Connect Remote IoT VPC AWS Not Working" can disrupt workflows and compromise operational efficiency.
- Security Breaches: Without proper security measures, your IoT devices are vulnerable to cyber threats.
- Data Loss: Secure connections are crucial for protecting sensitive data.
The good news is, with the right knowledge and tools, you can overcome these challenges.
RemoteIoT VPC SSH (Secure Shell) serves as a combination of tools and configurations that allow you to securely connect to your Raspberry Pi over the internet. Unlike paid services, RemoteIoT VPC SSH provides a cost-effective way to establish a secure and private connection to your IoT devices. Following this guide, you'll learn how to configure your VPC, manage access controls, and guarantee seamless communication between devices.
What makes RemoteIoT stand out is its commitment to accessibility. The "securely connect remote IoT VPC Raspberry Pi download free" concept refers to the availability of free tools and resources that can help you achieve this setup without incurring additional costs. In essence, this guide walks you through the steps to securely connect remote IoT devices to a VPC using a Raspberry Pi, all without any additional charges.
Lets address some of the common questions:
- What is a VPC? A VPC is a virtual network, providing a secure and isolated environment for your resources within a public cloud.
- Why is a secure connection important? A secure connection protects sensitive data and ensures the integrity of your IoT ecosystem.
- How does RemoteIoT work? RemoteIoT utilizes technologies like VPC and SSH to establish secure connections to your devices.
- What are the benefits of using a Raspberry Pi? The Raspberry Pi serves as a gateway, allowing you to connect and manage IoT devices remotely.
This article will explore the best practices, tools, and strategies to ensure a secure connection to your RemoteIoT VPC while maintaining high performance and reliability. With the rise of remote work and distributed systems, understanding how to securely connect a Raspberry Pi to your VPC is a valuable skill that can enhance your cybersecurity capabilities.
This guide will walk you through the process of securely connecting remote IoT devices using a Raspberry Pi on AWS VPC, ensuring robust protection for your network. By creating a VPC, you can control access to your devices and ensure that only authorized users can interact with them. This is particularly important when managing remote IoT devices that are spread across different locations.
We'll cover the following key areas:
- Setting up your VPC: This involves configuring the virtual network, subnets, and other necessary components.
- Configuring your Raspberry Pi: This includes installing the necessary software and configuring the device to connect to the VPC.
- Securing the connection: This involves implementing encryption and access control mechanisms.
- Managing Access Controls: Learn how to control who can interact with your devices.
- Ensuring Seamless Communication: Guarantee a smooth and reliable data flow between devices.
With the right tools and knowledge, you can create a secure and efficient network that meets your needs. Start exploring the potential of securely connecting RemoteIoT VPC Raspberry Pi today! And for more information, don't hesitate to visit the RemoteIoT website. Learn how to securely connect RemoteIoT VPC Raspberry Pi with a free download for Windows.
Here are a few important points to remember:
- Security is paramount: Never compromise on security when it comes to your IoT devices.
- Choose strong passwords: Implement strong passwords and regularly update them.
- Keep software updated: Update all software and firmware to the latest versions to patch security vulnerabilities.
- Monitor your network: Continuously monitor your network for any suspicious activity.
In conclusion, securing your remote IoT devices is a critical task in today's interconnected world. This article has provided a comprehensive guide to understanding the tools, strategies, and best practices needed to fortify your digital fortress. Remember, protecting your data and maintaining system integrity is not just a choice; it's a necessity in the digital age.
Article Recommendations


Detail Author:
- Name : Mac Volkman
- Username : herman.zulauf
- Email : garnett59@maggio.biz
- Birthdate : 1982-10-20
- Address : 492 Pollich Tunnel Suite 011 Robertshaven, ME 70977-9262
- Phone : 858-737-3040
- Company : Larkin-Kling
- Job : Washing Equipment Operator
- Bio : Nisi et sint est deserunt. Quasi asperiores deserunt eius molestiae non quasi minima dicta. Et corporis culpa quos earum dolores. Et magnam fuga deserunt.
Socials
linkedin:
- url : https://linkedin.com/in/nrempel
- username : nrempel
- bio : Vel est sunt quam eum perspiciatis sint.
- followers : 479
- following : 1513
instagram:
- url : https://instagram.com/rempeln
- username : rempeln
- bio : Consequatur praesentium doloremque mollitia non. Voluptatem provident ut itaque.
- followers : 2119
- following : 2614
facebook:
- url : https://facebook.com/newton_rempel
- username : newton_rempel
- bio : Quia dicta pariatur beatae ut.
- followers : 1084
- following : 1942
twitter:
- url : https://twitter.com/newton.rempel
- username : newton.rempel
- bio : Voluptatem doloremque at nihil voluptas fugiat cum iusto. Natus et rerum rerum. Et qui nam quas consectetur.
- followers : 6980
- following : 702
tiktok:
- url : https://tiktok.com/@newton_rempel
- username : newton_rempel
- bio : Neque rerum ea quos.
- followers : 3039
- following : 996